Written by Tim Burris, HCISPP, Product Manager, Privacy and Security - iatricSystems

As part of Cybersecurity Awareness Month, we've shared tips so far for "Owning It" with remote access security, "Securing It" with multi-factor authentication, and "Protecting It" against Phishing attacks, and the potential costs of a HIPAA violation. Today I want to talk about how having layers of patient privacy help keep Protected Health Information (PHI) safe.
Before I dive into that topic, I wanted to remind you that in ongoing support of National Cybersecurity Awareness Month, we hosted a series of five short 10-minute webinars each day the last week in October called "Cybersecurity Coffee Chats." We covered topics including remote access security, multi-factor authentication, phishing, and patient privacy.
Click this link to access the entire Cybersecurity coffee chat series.
So now let's move to the very important topic of protecting patient privacy. The layers of patient privacy aren't all that different in their approach to many security frameworks.
Many security frameworks demonstrate a layered approach to cyber security. They have different focuses and requirements stacked atop one another to demonstrate all the considerations that need to be made when it comes to an effective defense strategy. This approach helps us to visualize the individual cyber security components and hopefully spot areas for improvement in our defenses.
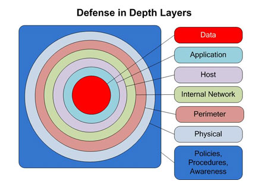
The framework for protecting Patient Privacy is similar. While it certainly overlaps with security in many regards, there is also a unique layered model laid out for us within HIPAA.
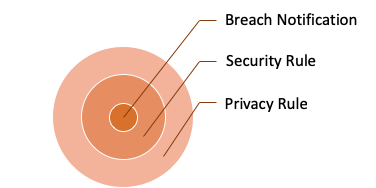
Layer 1 sets the foundation for everything else that is required. By defining what information must be protected, and ways that it can be protected, it serves to give us focus for subsequent layers. Specifically, the privacy rule addresses the following:
Layer 2 focuses on one of the requirements outlined in the Privacy Rule – Data Safeguards. Now that we know what information is at stake, and what our obligations are, the Security Rule focuses on how we can keep patient information safe. It addresses the following:
The top layer is for Breach Notifications. This layer establishes the rules for identifying breaches, evaluating breaches for exceptions, and reporting breaches to the appropriate entities when they occur. While Breach Notification is certainly something that no organization wants to engage in, it is an important requirement associated with HIPAA. It provides a tangible incentive to protect patient information. The financial penalties and loss in reputation associated with a breach can be a painful lesson for any organization. It serves as an effective motivator to solidify the lower layers.
This layer specifically addresses the following:
As organizations, we have a responsibility to protect patient information. HIPAA doesn’t just provide the rules we must follow, but a framework with HOW we can follow them, as well as the penalties when we don’t comply. Understand and implement these layers of defense in your organization and your patients will be better protected.
You can watch the recording of "The Layers of Patient Privacy" webinar below.
{% video_player "embed_player" overrideable=False, type='scriptV4', hide_playlist=True, viral_sharing=False, embed_button=False, width='1920', height='1080', player_id='19897952721', style='' %}Click this link to access the entire Cybersecurity coffee chat series.